In the UAE’s dynamic business landscape, where cross-border transactions and international investments flourish, secure data room management has emerged as a critical infrastructure for modern business operations. The global virtual data room market, valued at $2.9 billion in 2024, reflects the growing recognition that traditional file-sharing methods are insufficient for today’s complex business transactions. As cybersecurity threats increase by 34% annually and data breaches cost organizations an average of $4.88 million, the need for robust, secure document management solutions has never been more pressing.
For investors and stakeholders operating in the UAE’s financial centers, particularly within the Dubai International Financial Centre (DIFC) and Abu Dhabi Global Market (ADGM), secure data room management represents more than a technological upgrade—it’s a strategic necessity for maintaining competitive advantage and regulatory compliance. Organizations that implement professional data room solutions report a 352% return on investment over three years, alongside 40% faster deal closure times and 67% reduction in security breach risks.
Understanding Virtual Data Rooms in Modern Business Transactions
Evolution from Physical to Virtual Data Rooms
The transformation from physical to virtual data rooms represents one of the most significant shifts in business transaction methodology. Traditional physical data rooms, once the gold standard for due diligence processes, required stakeholders to travel to specific locations, review documents under supervision, and manage cumbersome paper-based systems. This approach created inherent limitations: geographic constraints, time zone conflicts, and substantial operational overhead.
Virtual data rooms have revolutionized this paradigm by providing secure, cloud-based repositories that enable 24/7 access from anywhere in the world. Modern VDRs support real-time collaboration among geographically dispersed teams, with 73% of users accessing data rooms via mobile devices.
This shift has proven particularly valuable for UAE-based businesses engaging in international transactions, where stakeholders may be located across multiple continents and time zones.
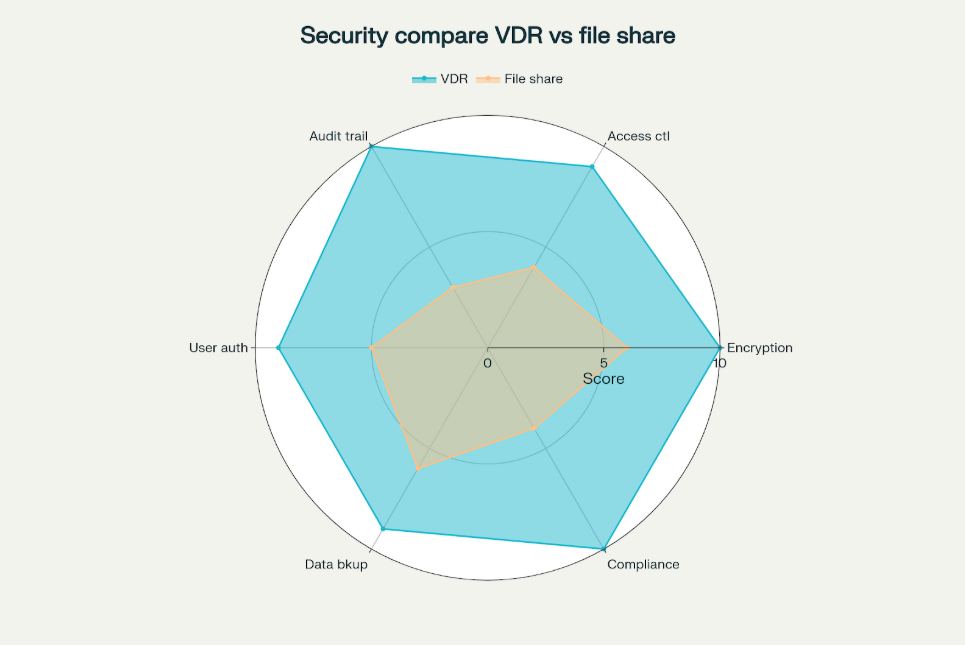
The evolution has also introduced sophisticated security measures that surpass traditional methods. While physical data rooms relied primarily on physical security and human oversight, virtual data rooms implement multi-layered security protocols including AES 256-bit encryption, two-factor authentication, and comprehensive audit trails. These technological advances have resulted in VDRs achieving 95% security effectiveness compared to 60% for traditional file-sharing methods.
Key Components of Secure Data Room Infrastructure
Modern virtual data rooms are built upon several foundational components that ensure both security and functionality. The infrastructure typically includes:
Cloud-Based Architecture: Leading VDR providers utilize georedundant servers with 99.97% uptime guarantees, ensuring continuous availability for critical business transactions. This architecture provides scalability that adapts to varying transaction sizes and user loads.
Advanced Encryption Protocols: Data protection involves multiple layers of encryption, including TLS 1.2 for data in transit and AES 256-bit encryption for data at rest. These protocols ensure that sensitive information remains protected even in the event of unauthorized access attempts.
Granular Access Controls: Modern VDRs implement role-based access control (RBAC) systems that allow administrators to define permissions at the document, folder, and user levels. This granular approach ensures that stakeholders only access information relevant to their role in the transaction.
Audit and Compliance Systems: Comprehensive logging systems track all user activities, document access, and system changes. These audit trails are essential for regulatory compliance and provide valuable insights into stakeholder engagement during due diligence processes.
Regulatory Compliance Requirements in UAE
The UAE’s regulatory environment presents unique challenges and opportunities for secure data room management. The Personal Data Protection Law (PDPL), implemented under Federal Decree-Law No. 45 of 2021, establishes comprehensive data protection requirements that align closely with international standards like GDPR.
DIFC and ADGM Specific Requirements: Financial institutions operating within the DIFC and ADGM must comply with additional regulatory frameworks. The DIFC Data Protection Law No. 5 of 2020 and ADGM’s data protection regulations require specific safeguards for client data, with non-compliance penalties reaching up to $25,000.
Cross-Border Data Transfer Regulations: UAE businesses engaging in international transactions must ensure that data transfers comply with both local and international regulations. This includes implementing appropriate safeguards for data sovereignty and ensuring that VDR providers maintain data residency options within approved jurisdictions.
Sector-Specific Compliance: Different industries face varying compliance requirements. Healthcare organizations must adhere to patient data protection standards, while financial services firms must comply with Central Bank of UAE regulations and international banking standards.
Critical Security Features for Business Transaction Success
Multi-layered Encryption and Access Controls
The foundation of secure data room management lies in robust encryption and access control mechanisms. Modern VDRs implement multiple security layers that work in concert to protect sensitive information throughout the transaction lifecycle.
Encryption at Rest and in Transit: Data stored within virtual data rooms is protected using AES 256-bit encryption, the same standard used by government agencies and financial institutions worldwide. During transmission, TLS 1.2 encryption ensures that data remains protected as it travels between users and servers. This dual-layer approach provides comprehensive protection against both storage-based and transmission-based attacks.
Dynamic Watermarking: Advanced VDRs implement dynamic watermarking that embeds user-specific information into documents, including IP addresses, timestamps, and user identifications. This feature serves both as a deterrent to unauthorized sharing and as a forensic tool for tracking document distribution.
Information Rights Management (IRM): IRM capabilities extend security controls beyond the data room environment, ensuring that documents retain their security properties even after download. This includes restrictions on printing, copying, and forwarding, with the ability to revoke access to downloaded documents remotely.
Advanced Authentication and User Management
User authentication represents a critical control point in data room security. Modern systems implement multi-factor authentication (MFA) as standard practice, requiring users to provide multiple forms of identification before gaining access.
Single Sign-On (SSO) Integration: For organizations using enterprise authentication systems, VDRs support SSO integration with popular platforms including Active Directory, Okta, and Azure Active Directory. This integration streamlines user access while maintaining security standards and reducing password-related vulnerabilities.
Biometric Authentication: Advanced VDR implementations are beginning to incorporate biometric authentication methods, including fingerprint and facial recognition systems. These technologies provide additional security layers while improving user experience through faster authentication processes.
Session Management: Sophisticated session management systems monitor user behavior patterns and automatically terminate sessions that exhibit suspicious activity. This includes detection of unusual access patterns, concurrent logins from different locations, and attempts to access restricted information.
Audit Trails and Activity Monitoring
The Federal Tax Authority’s enforcement capabilities have expanded significantly. Detailed record-keeping needs. Transfer pricing documentation. Audit preparation consume operational resources. Startups receiving inquiries must respond promptly with detailed documentation. This disrupts normal business operations.
Real-time Monitoring: Advanced monitoring systems provide real-time alerts for suspicious activities, including multiple failed login attempts, unusual download patterns, and access attempts from restricted geographic locations. These systems enable rapid response to potential security incidents.
Behavioral Analytics: Machine learning algorithms analyze user behavior patterns to identify anomalies that may indicate security threats or compliance violations. This proactive approach to security monitoring helps organizations address potential issues before they escalate.
Compliance Reporting: Automated compliance reporting tools generate detailed reports that demonstrate adherence to regulatory requirements. These reports can be customized to meet specific audit requirements and provide evidence of due diligence in data protection practices.
Optimizing Data Room Management for Investor Relations
Organizing Documents for Efficient Due Diligence
Effective document organization is crucial for streamlining due diligence processes and maintaining investor confidence. Research indicates that well-organized data rooms can reduce due diligence time by 3-4 hours daily, significantly accelerating deal timelines.
Standardized Folder Structures: Leading VDR providers offer pre-configured folder structures based on industry best practices and transaction types. For M&A transactions, this typically includes sections for financial statements, legal documents, operational information, and regulatory filings. These standardized structures reduce setup time and ensure consistency across transactions.
Automated Document Indexing: AI-powered indexing systems automatically categorize and tag documents based on content analysis, reducing manual organization efforts and improving search functionality. This automation is particularly valuable for large transactions involving thousands of documents.
Version Control Systems: Robust version control ensures that stakeholders always access the most current document versions while maintaining historical records of changes. This capability is essential for maintaining audit trails and ensuring data integrity throughout the transaction process.
Streamlining Communication and Q&A Processes
Efficient communication management is essential for maintaining transaction momentum and stakeholder engagement. Modern VDRs incorporate sophisticated communication tools that facilitate seamless interaction between all parties.
Integrated Q&A Systems: Built-in Q&A functionality allows investors to submit questions directly within the data room environment, with responses tracked and managed through the system. This integration eliminates the need for external communication tools while maintaining complete records of all interactions.
Automated Workflow Management: Workflow automation ensures that questions are routed to appropriate subject matter experts and that responses are provided within agreed timeframes. This systematic approach prevents communication delays that can derail transaction timelines.
Multi-language Support: For international transactions, VDRs increasingly offer multi-language support, including automatic translation capabilities for document content and user interfaces. This feature is particularly valuable for UAE-based businesses engaging with global investors.
Real-time Collaboration Tools and Features
Modern business transactions require real-time collaboration capabilities that enable stakeholders to work together effectively regardless of geographic location or time zone differences.
Simultaneous Document Review: Advanced VDRs support simultaneous document review by multiple users, with real-time commenting and annotation capabilities. This functionality enables collaborative analysis and faster decision-making processes.
Video Conferencing Integration: Integration with popular video conferencing platforms allows stakeholders to conduct virtual meetings directly within the data room environment, maintaining security while facilitating face-to-face communication.
Mobile Accessibility: With 73% of users accessing data rooms via mobile devices, responsive design and dedicated mobile applications ensure that stakeholders can participate in transactions from anywhere.
Stakeholder Management and Access Control Strategies
Role-based Permission Systems
Effective stakeholder management requires sophisticated permission systems that balance security with accessibility. Modern VDRs implement granular role-based access controls that can be customized based on stakeholder requirements and transaction specifics.

Hierarchical Permission Structures: Organizations can establish hierarchical permission structures that reflect organizational relationships and transaction roles. For example, senior executives may have broader access rights than junior team members, while external advisors may be restricted to specific document categories.
Dynamic Permission Adjustment: Advanced systems allow administrators to adjust permissions dynamically throughout the transaction lifecycle. This capability is particularly valuable for phased due diligence processes where access rights may need to change as transactions progress.
Automated Permission Management: Rule-based permission management systems automatically assign access rights based on predefined criteria, reducing administrative overhead and ensuring consistency in access control implementation.
Time-sensitive Access Controls
Many business transactions involve time-sensitive information that requires temporary access controls. Modern VDRs provide sophisticated time-based access management capabilities that enhance security while maintaining operational flexibility.
Scheduled Access Activation: Administrators can schedule access rights to activate and deactivate at predetermined times, ensuring that stakeholders only have access during authorized periods. This feature is particularly valuable for managing access during non-business hours or across different time zones.
Automatic Access Expiration: Access rights can be configured to expire automatically after specified periods, reducing the risk of unauthorized access to outdated information. This capability is essential for maintaining security throughout extended transaction processes.
Time-based Document Releases: Documents can be configured for automatic release at predetermined times, enabling phased information disclosure that aligns with transaction milestones and regulatory requirements.
Geographic and IP-based Restrictions
Geographic access controls provide additional security layers by restricting access based on user location or IP address. This capability is particularly valuable for organizations operating in regulated industries or dealing with sensitive government information.
Country-based Access Restrictions: Administrators can restrict access based on country of origin, ensuring compliance with export control regulations and data sovereignty requirements. This feature is essential for UAE businesses dealing with international sanctions or restricted technology transfers.
IP Whitelisting: Organizations can maintain approved IP address lists, ensuring that access is only permitted from authorized locations. This capability is particularly valuable for organizations with strict security policies or regulatory requirements.
VPN Detection and Management: Advanced systems can detect and manage VPN usage, providing flexibility for legitimate business use while maintaining security controls for unauthorized access attempts.
Cost-Benefit Analysis: In-House vs. Professional Data Room Services
TCO Comparison and ROI Metrics
The decision between developing in-house data room capabilities versus engaging professional services requires careful analysis of total cost of ownership (TCO) and return on investment (ROI) metrics.
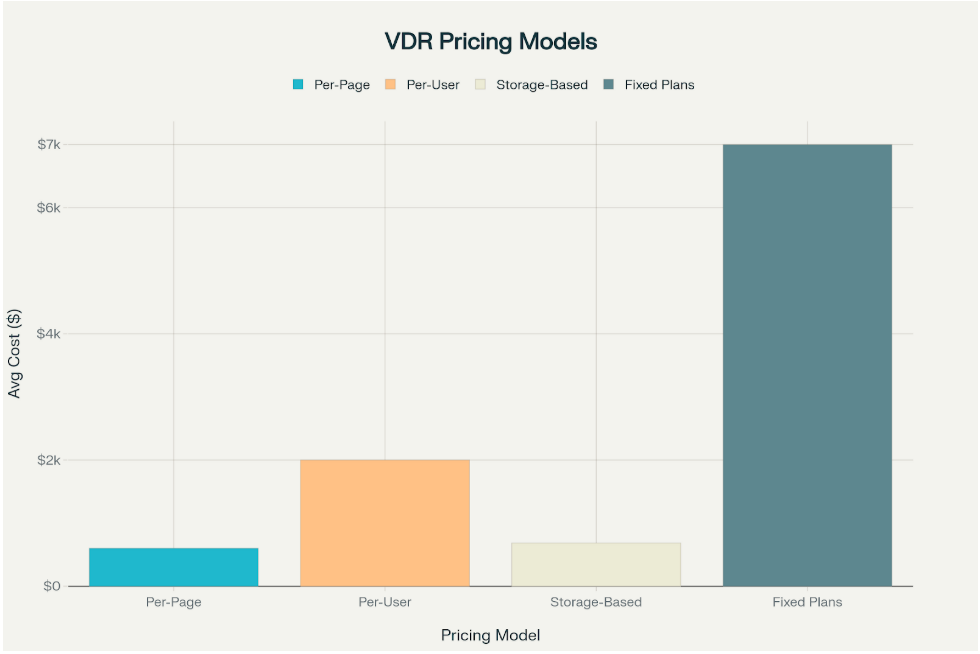
Initial Investment Comparison: Developing in-house data room capabilities requires significant upfront investment in technology infrastructure, security systems, and personnel. Professional data room services offer immediate access to enterprise-grade capabilities without capital expenditure, with pricing models ranging from $400-$10,000 monthly depending on features and scale.
Operational Cost Analysis: In-house solutions require ongoing maintenance, security updates, and personnel costs. Professional services include these operational elements within their service offerings, providing predictable monthly costs and eliminating the need for specialized internal resources.
Scalability Considerations: Professional data room services offer scalability advantages, allowing organizations to adjust capacity based on transaction volume without infrastructure investment. This flexibility is particularly valuable for organizations with variable transaction activities.
ROI Metrics: Organizations using professional data room services report average ROI of 352% over three years, driven by reduced transaction times, improved security, and enhanced stakeholder satisfaction. These metrics demonstrate the value proposition of professional services beyond simple cost considerations.
Risk Mitigation and Compliance Benefits
Professional data room services provide significant risk mitigation and compliance benefits that are often difficult to quantify but essential for business operations.
Security Risk Reduction: Professional services implement enterprise-grade security measures that would be prohibitively expensive for individual organizations to develop and maintain. This includes 24/7 security monitoring, threat detection systems, and incident response capabilities.
Compliance Assurance: Professional VDR providers maintain compliance with multiple regulatory frameworks, including ISO 27001, SOC 2, and GDPR. This comprehensive compliance coverage ensures that organizations meet regulatory requirements without developing internal compliance capabilities.
Business Continuity: Professional services provide business continuity assurance through redundant infrastructure and disaster recovery capabilities. This assurance is essential for mission-critical business transactions where downtime can result in significant financial losses.
Implementation Best Practices and Common Pitfalls
Step-by-Step Setup Guide
Successful data room implementation requires systematic planning and execution. Organizations should follow established best practices to ensure optimal results and avoid common implementation pitfalls.
Pre-Implementation Planning: Effective implementation begins with comprehensive planning that includes stakeholder identification, document inventory, and security requirements assessment. This planning phase typically requires 2-3 weeks for complex transactions but ensures smooth implementation and user adoption.
Configuration and Customization: Data room configuration should reflect organizational branding and workflow requirements. This includes custom folder structures, user role definitions, and integration with existing business systems. Modern VDRs can be configured and operational within 10 minutes, though comprehensive customization may require additional time.
User Training and Adoption: Comprehensive user training is essential for successful implementation. This includes training for administrators, end-users, and support personnel. Professional VDR providers typically offer comprehensive training programs and ongoing support to ensure successful adoption.
Testing and Validation: Thorough testing should be conducted before going live, including security testing, user acceptance testing, and performance validation. This testing phase helps identify and resolve issues before they impact business operations.
Document Organization and Version Control
Effective document organization is crucial for user adoption and transaction efficiency. Organizations should implement systematic approaches to document management that reflect best practices and user requirements.
Standardized Naming Conventions: Consistent naming conventions improve document discoverability and reduce confusion. This includes standard prefixes, date formats, and version identifiers that enable users to quickly identify and access relevant documents.
Logical Folder Structures: Folder structures should reflect the logical flow of due diligence processes and stakeholder needs. This typically includes separation by function (legal, financial, operational) and by audience (all users, restricted access, management only).
Version Control Protocols: Robust version control ensures that stakeholders always access current information while maintaining historical records. This includes automated version tracking, approval workflows, and change notifications.
User Training and Support Protocols
Comprehensive user training and support are essential for successful data room implementation and ongoing operation. Organizations should develop systematic approaches to user enablement that ensure optimal utilization of data room capabilities.
Role-based Training Programs: Training programs should be tailored to user roles and responsibilities, ensuring that each user group receives relevant instruction. This includes separate training for administrators, end-users, and support personnel.
Ongoing Support Systems: Continuous support systems should be established to address user questions and technical issues. Professional VDR providers typically offer 24/7 support with average response times of 36 minutes.
Performance Monitoring: Regular performance monitoring helps identify user adoption issues and optimization opportunities. This includes tracking usage metrics, user satisfaction surveys, and system performance indicators.
Future of Secure Data Room Technology
AI-Powered Document Analysis
Artificial intelligence is transforming data room capabilities by automating routine tasks and providing intelligent insights that enhance decision-making processes. AI integration growth has reached 47% in the data room market, reflecting the significant value these technologies provide.
Automated Document Classification: AI systems can automatically categorize and tag documents based on content analysis, reducing manual organization efforts and improving search functionality. This automation is particularly valuable for large transactions involving thousands of documents.
Intelligent Content Analysis: Advanced AI systems can analyze document content to identify key terms, extract relevant data, and generate summaries that help stakeholders quickly understand document importance and relevance.
Predictive Analytics: AI-powered analytics can predict transaction outcomes based on stakeholder behavior patterns, document access trends, and historical transaction data. These insights help organizations optimize their transaction strategies and improve success rates.
Natural Language Processing: NLP capabilities enable sophisticated search functionality that understands context and meaning, allowing users to find relevant information using natural language queries rather than specific keywords.
Blockchain Integration for Enhanced Security
Blockchain technology is emerging as a significant enhancement to data room security, providing immutable audit trails and enhanced trust mechanisms for sensitive business transactions.
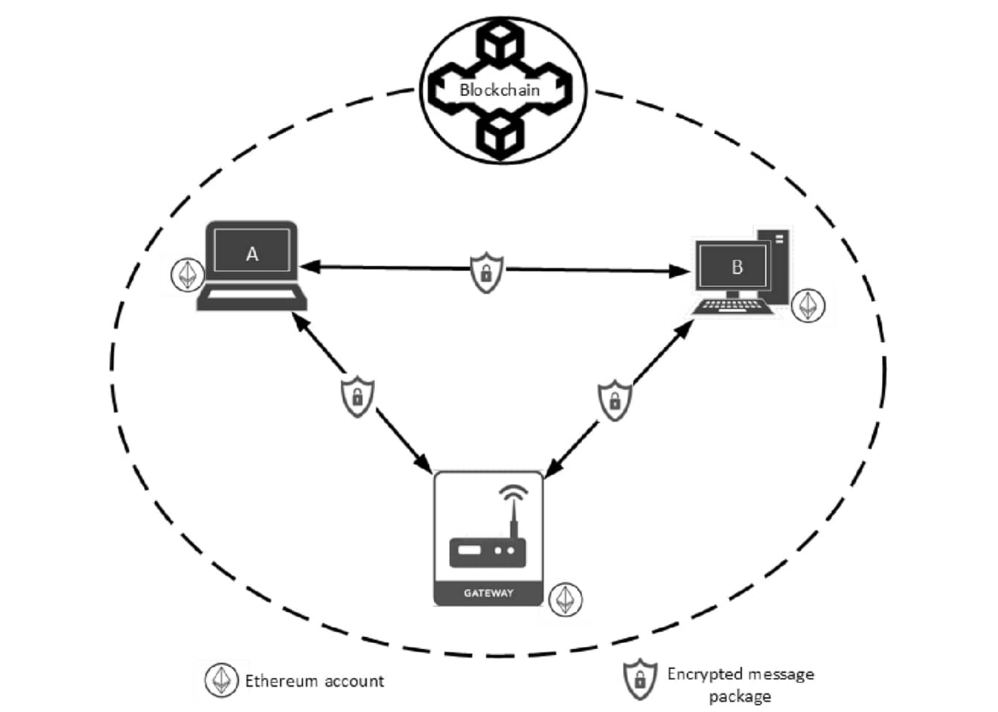
Immutable Audit Trails: Blockchain-based audit trails provide tamper-proof records of all data room activities, ensuring that transaction histories cannot be altered or deleted. This capability is particularly valuable for regulatory compliance and dispute resolution.
Smart Contract Integration: Smart contracts can automate routine data room processes, including access control, document release schedules, and compliance verification. This automation reduces administrative overhead while ensuring consistent process execution.
Decentralized Identity Management: Blockchain-based identity management systems provide enhanced security for user authentication while reducing reliance on centralized identity providers. This approach improves security while maintaining user privacy.
Enhanced Data Integrity: Blockchain technology provides cryptographic proof of data integrity, ensuring that documents have not been tampered with during storage or transmission. This capability is essential for maintaining trust in sensitive business transactions.
The integration of blockchain technology in data rooms represents a significant advancement in secure document management, with adoption rates reaching 28% among leading VDR providers. As this technology matures, it will likely become a standard feature in enterprise-grade data room solutions.
Conclusion
Secure data room management has evolved from a luxury to a necessity in today’s complex business environment. For investors and stakeholders operating in the UAE’s dynamic financial centers, the implementation of professional data room solutions provides essential capabilities for managing sensitive information, ensuring regulatory compliance, and facilitating successful business transactions.

The compelling business case for professional data room services is demonstrated through measurable benefits: 352% ROI over three years, 40% reduction in transaction times, and 67% improvement in security breach prevention. These metrics reflect the tangible value that modern VDR solutions provide to organizations serious about protecting their most sensitive business information.
As the global virtual data room market continues its projected growth trajectory toward $10.2 billion by 2033, organizations that invest in secure data room management today will be well-positioned to capitalize on future opportunities while maintaining the highest standards of security and compliance.
For UAE-based businesses and international investors seeking to optimize their transaction processes while ensuring robust security and compliance, partnering with experienced data room providers like Jazaa represents a strategic investment in operational excellence and competitive advantage. The combination of advanced technology, comprehensive security measures, and local regulatory expertise positions such partnerships as essential components of successful business strategies in the digital age.





